“Your System Was Breached By Remote Desktop Protocol” Email Scam: What You Need to Know
Sextortion scams are one of the most alarming forms of cyber fraud, preying on fear and embarrassment to coerce victims…
G700 Android Malware: Removal and Prevention
G700 is a high-end Remote Access Trojan (RAT) that targets Android devices, causing a range of malicious activities, including data…
SyncRemote Adware: Understanding the Threat and Protecting Your System
SyncRemote is a newly identified adware application belonging to the AdLoad malware family. Discovered during an analysis of submissions to…
ElementEntry Adware Overview
ElementEntry is a type of adware that belongs to the AdLoad malware family. Adware, or advertising-supported software, is specifically designed…
FormatLocator Adware: Overview and Threat Assessment
FormatLocator is a malicious adware program that primarily targets Mac users, delivering intrusive and often deceptive advertisements. This type of…
GlobalHelper Adware Overview
GlobalHelper is a type of adware that infiltrates computers, primarily Macs, to deliver intrusive advertisements. Applications like GlobalHelper typically operate…
What Is Unbosperismoles.co.in?
Unbosperismoles.co.in is a suspicious and potentially harmful domain associated with browser hijackers, adware, and other potentially unwanted programs (PUPs). It…
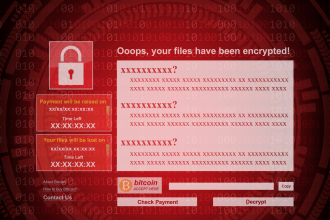
Aptlock Ransomware: Understanding, Removing, and Preventing Future Infections
Aptlock ransomware is a notorious malware threat designed to encrypt files on infected computers and extort ransom payments from victims…
The $DOGE Airdrop Scam: Understanding the Threat, Removal, and Prevention
Cryptocurrency scams have been an increasing issue in the digital world. Among these scams is the fake $DOGE Airdrop that…
What is Lsma22.exe? Removal and Prevention
The name Lsma22.exe might seem innocent at first glance, but it’s associated with a severe cyber threat. This file is…