Claim Aerodrome Rewards Scam: Understanding the Threat and How to Protect Yourself
Яcams and cyber threats are becoming increasingly sophisticated, targeting unsuspecting users through various means. One such threat is the Claim…
SmartColor Password Expiry Email Scam: A Cybersecurity Overview
Phishing scams are deceptive tactics used by cybercriminals to trick individuals into divulging sensitive information or installing malicious software. These…
Understanding and Removing the Claim Eigen Scam
The Claim Eigen scam is designed to deceive users into divulging sensitive information or installing malicious software on their devices.…
“Confirm That This Is Your Valid Email Address” Phishing Scam
Phishing scams are deceptive tactics used by cybercriminals to steal sensitive information, such as login credentials or financial data, by…
“Website Suspension In Progress” Email Scam: Defending Against Phishing Attacks
Phishing scams typically infiltrate systems through malicious links or attachments contained in seemingly credible communications. Once an individual interacts with…
“I’ve Got Access to Your Smartphone” Email Scam
Phishing scams come in various forms, all designed to deceive and manipulate individuals into revealing sensitive information or installing malware.…
Missed Call Voicemail Alert Scam
Phishing scams are deceitful tactics used by cybercriminals to exploit individuals by tricking them into revealing sensitive information or installing…
Rothschild Foundation Email Scam: An Insidious Cyber Security Threat
Phishing scams are deceptive tactics used by cybercriminals to trick individuals into revealing sensitive information or installing malware. These scams…
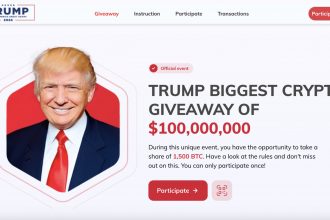
The Elon Musk and Donald Trump Crypto Giveaway Scam: What You Need to Know
In recent months, a new cyber scam has emerged, preying on the popularity of high-profile figures such as Elon Musk…
“Your Device Is At Risk” Pop-Up Scam Threat on Mac
Cyber threats are becoming increasingly sophisticated, and one of the more deceptive forms is the "Your Device Is At Risk"…