Giggle Pop-Up Scam: A Malicious Virus Threat
Pop-up scams have become increasingly prevalent, preying on unsuspecting users. These scams…
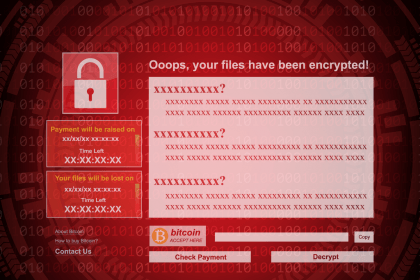
Understanding and Removing The Bully Ransomware
Ransomware is a notorious form of malware that encrypts files on a…
“Can Stealer” Malware Threat: Detailed Guide, Removal, and Prevention
Can Stealer is a malicious software categorized as a password-stealing trojan designed…
Understanding and Combatting Trojan Horse Malware: A Focus on TrojanWin32.Leonem
Trojan horse malware, commonly referred to as "Trojans," represents a broad category…
How to Protect Your Computer from Unauthorized File Downloads: Comprehensive Removal Guide and Prevention Tips
Cyber threats are becoming more sophisticated and pervasive. One of the most…
BrowserConnection Adware: An Introduction
Adware, short for advertising-supported software, is a type of malware designed to…
MegaGuard Adware: Understanding the Threat and Ensuring Your Security
Cyber threats come in various forms, each posing unique risks to users'…
RomanceRocket Click Ads Malware
RomanceRocket Click Ads is a form of adware that infiltrates systems to…
Understanding and Removing the Watz File Virus
The Watz File Virus, a notorious type of ransomware, has been causing…
Findfrlarex.com: Comprehensive Guide to Understanding and Removing the Redirect
In recent times, many users have reported encountering an unwanted redirect to…