Clickads-hub[.]top Ads
Clickads-hubtop is a deceptive website designed to lure users into granting permission to display its notifications. These notifications are not…
Sos-bg-sof-1.exo.io: Understanding and Removing This Dangerous Threat
The internet is full of various dangers, from harmful malware to intrusive pop-ups that try to steal your data. One…
What Is Xx.knit.bid and How to Remove It?
Xx.knit.bid is a deceptive and harmful website that masquerades as an adult AI-based Japanese platform. Its primary aim is to…
F95.zone: A Deceptive Threat to Your Online Security
The digital landscape is rife with malicious entities posing threats to user safety, and F95.zone is no exception. This site…
Xxxz.tv Redirect Virus: A Detailed Guide on How to Remove It and Protect Your System
The internet is a vast place, and while it offers countless opportunities for communication, entertainment, and education, it also harbors…
How to Protect Your System from mefearcates.com Ads and Deceptive Push Notifications
Websites like mefearcatescom have become a significant concern for internet users. These malicious sites rely on social engineering tactics to…
Strave App: Threat Analysis and Removal Guide
The Strave App is a potentially unwanted program (PUP) that can cause various issues for users who unknowingly install it.…
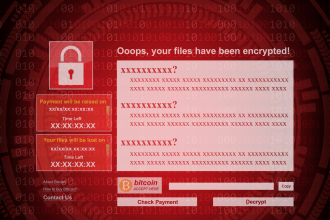
Held Ransomware: Detection, Removal, and Prevention
Held ransomware, a member of the infamous Djvu family, is a malicious program designed to encrypt victims' files and demand…
Kixtixcy Ransomware: Analysis and Removal Guide
Kixtixcy ransomware, a new strain of the notorious Dharma ransomware family, is a sophisticated threat designed to encrypt files, rename…
Vulcan Ransomware: A Threat Analysis and Removal Guide
What is Vulcan Ransomware? Vulcan is a ransomware variant designed to encrypt files on a victim’s device, rendering them inaccessible…