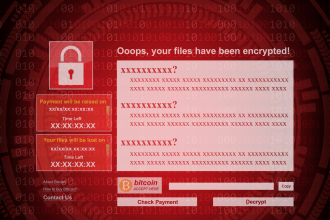
AllCiphered Ransomware: A Detailed Overview and Removal Guide
AllCiphered is a variant of the notorious MedusaLocker ransomware family, a type of crypto-malware that encrypts files on infected systems…
Zephyr Miner: A Cryptocurrency Miner Malware Threat
Cryptocurrency miners, also known as cryptominers, are increasingly becoming a significant cybersecurity threat due to their ability to covertly exploit…
SMOK Ransomware: A Dangerous Crypto Virus Threat
SMOK is a type of ransomware that encrypts files on the victim’s computer and demands a ransom for decryption. As…
AdBlocker Professional Adware
In the world of digital tools, ad blockers are often seen as essential for improving browsing experiences by removing unwanted…
Imploder Ransomware: A Growing Threat to Your Files
Imploder is a newly discovered ransomware that has raised concern among cybersecurity experts. Unlike typical ransomware, which is designed to…
Pro Video Downloader: A Dangerous Adware Threat
Pro Video Downloader is an extension promoted as a convenient tool for downloading online videos in various formats and resolutions.…
ViT Ransomware: How to Detect, Remove, and Protect Against This Dangerous Threat
ViT ransomware, part of the notorious Xorist family, is a highly destructive malware that encrypts victims' files and demands a…
Revive Ransomware: How to Remove It and Prevent Future Infections
Ransomware remains one of the most alarming forms of malware, targeting both individuals and organizations by encrypting critical data and…
MAGA Ransomware: A Comprehensive Guide to Detection, Removal, and Prevention
Ransomware attacks are among the most devastating forms of cyber threats, capable of encrypting files and demanding ransoms to regain…
Heur.AdvML.b: Understanding the Threat and How to Remove It
Heur.AdvML.b is a heuristic detection name assigned by antivirus software to flag files that exhibit behaviors or characteristics resembling malware.…